The following diagram depicts entities involved in delivering the global eduroam service.
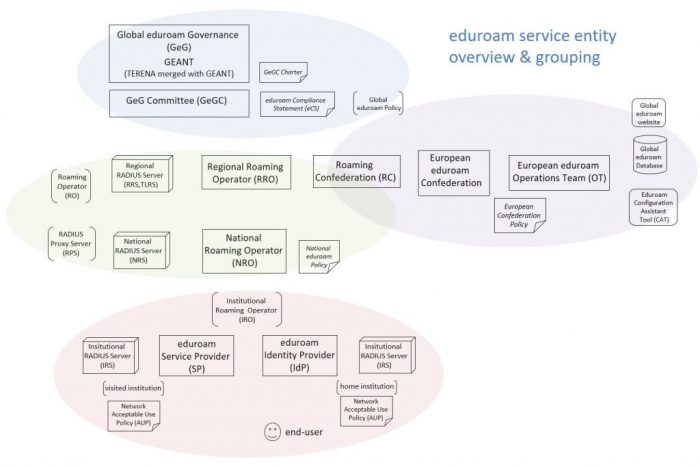
At the top are the global governance, global policy, and globally shared resources. Global governance interacts with the next layer, “roaming operators”, which may be either regional (e.g. APAN) or national (e.g. eduroam AU). National Roaming Operators (NROs) are associated with one regional roaming operator.
In the middle to the right-hand side the European eduroam Confederation is identified separately as it has an established role in global operations, having developed resources & tools that are globally shared (e.g. global eduroam website, global database, configuration assistant tool (CAT), and value added services such as the “Managed IdP” service).
At the bottom institutional participants are depicted, and the two roles a participant may fulfil are identified: “Service Provider” (SP) and “Identity Provider” (IdP)
From a technical perspective, the eduroam service may be considered as having two distinct functions, corresponding to those institutional roles:
- provision of an IEEE 802.1x network service, most commonly a Wi-Fi network with common network name “eduroam”, which end-users access to via their mobile devices; and
- provision of a remote authentication infrastructure at institutional, national and regional levels, enabling IEEE 802.1x authentication of those end-users to be performed globally.
The “eduroam” network service is provided by institutions performing the eduroam SP role.
The IdP role is fundamentally the authentication of end-users. The remote authentication infrastructure is provided jointly by institutions (both IdPs and SPs), and national and regional roaming operators, being a hierarchy of institutional, national and regional RADIUS Servers.
The eduroam service is a ‘global trust federation’, where SPs and IdPs trust each other and the national and regional roaming operators in performing their roles in full compliance with technical and administrative policies. Global governance, which includes representatives of each eduroam region, is responsible for establishing the global policy, and NROs for establishing national eduroam policies aligned to the global policy.
The roles and responsibilities of an eduroam Identity Provider and Service Provider are detailed below.
Basic Principals
Remote Authentication
As stated in the eduroam Compliance Statement (the global policy that NROs are required to sign), the eduroam service is provided for end-users engaged in research and/or education. eduroam enables end-users to travel globally and connect to visited participating institutions’ eduroam networks easily and securely, and enjoy a reasonably consistent quality of service delivered by the visited institution eduroam network. Use of a common network name “eduroam” enables end-user devices to be configured to automatically connect to the eduroam network when it is available.
The technical solution for eduroam (IEEE 802.1X, RADIUS) enables remote authentication to be performed, routed from visited institution (SP) via national and regional infrastructure to the user’s home institution (IdP), based on the institutional realm part of the eduroam username, the eduroam username being of the form <institutional_username>@<institutional_realm>.
Use of tunnelled protocols to convey username/password credentials (e.g. EAP-PEAP/MSCHAVP2, EAP-TTLS/PAP) delivers end-user and IdP security, as institutional credentials remain secret between the end-user device and the user’s home institution RADIUS server.
The eduroam “Configuration Assistant Tool” is available for institutions globally to ensure end-user devices are configured for eduroam authentication securely and consistently. An important security requirement is that the user’s ‘home institution’ RADIUS server is authenticated by their device during the authentication process.
End-User Accountability & Traceability
The eduroam Compliance Statement states that IdPs are responsible for the actions of their users in accessing a visited institution’s “eduroam” network.
Both IdPs and SPs are required to have and publish their institutional network “Acceptable Use Policy” (AUP). Given the closed community of end-users of eduroam being engaged in research and/or education, and eligibility requirements of IdPs and SPs, there an implicit assumption of reasonable equivalence of IdP and SP AUPs.
A pre-requisite for IdP participation is that end-users have a contractual requirement to comply with their home institution’s network AUP while using the home institution’s network with consequences for non-compliance made clear to end-users. eduroam IdPs must extend this requirement for their end-user AUP compliance, and consequences of non-compliance, to use of eduroam networks at SPs.
In order to enable traceability from a network access event at an SP to an authentication event and the individual user at an IdP, IdPs are required by global policy to capture and retain RADIUS server logs. RADIUS logs’ timestamps must be in UTC to avoid confusion, and the “Calling-Station-Id” attribute must contain the end-user device MAC address. SPs are recommended to capture and retain RADIUS server logs to enable traceability, however it is recognised that SPs may have local policy meaning they choose not to have such end-user traceability.
Institutional Participant Types
Institutions may participate in eduroam AU as one of 3 types: IdP+SP, SP-Only, IdP-Only.
Most institutions participating in eduroam are directly engaged in education and/or research, and have an institutional network and are willing and able to perform both IdP and SP roles, i.e. be IdP+SP participants.
If an institution is not directly engaged in R&E, i.e. its users are not engaged in education and/or research hence not eligible to be eduroam end-users, yet there is a business case for providing an “eduroam” network for visiting R&E users, it can operate as an SP-Only participant. Institutions which typically participate in eduroam AU as SP-only operators are health institution, libraries, cultural spaces (museums, art-galleries), public spaces (e.g. local government Wi-Fi locations), public-transport (air-ports, buses, ferries).
An institution will only be accepted as an IdP-only participant in eduroam AU if it is agreed by AARNet that it is infeasible or there is substantially no benefit to R&E visitors in providing an eduroam network on the IdP-only institution site. If an institution operates as an IdP, it should also operate as an SP to respect the ‘give-and-take’ nature of the eduroam service based on eduroam network access costs being born by the SP. the rationale being if an institution wishes its users to be able to roam and access networks at visited institutions, that institutions should also be willing to provide an eduroam network for access by R&E visitors.
Institutional Eligibility
As a global service, eduroam is governed by a global policy which states that eduroam is for users from “organisations engaged in research and/or education”. Clearly this constitutes a closed but very large global user community. This requirement defines the fundamental eligibility requirement for institutions participating as IdPs.
The global policy also states that the NRO can determine eligibility of IdPs and SPs to participate in the national eduroam service.
The eduroam AU national policy requires that eligibility for eduroam AU IdP participation is restricted to AARNet customers. Institutions under an AARNet Access Agreement and satisfying IdP prerequisites described below may operate as an eduroam AU IdP.
Any institution with an identified valid (based on AARNet’s judgement) business case for participating in eduroam AU and satisfying SP pre-requisites described below may operate as an eduroam AU SP.
Institutional Roles & Responsibilities
Institutional roles and responsibilities are described below in detail, categorised as general (common to IdP and SP), IdP, or SP.
General
Both eduroam AU IdPs and SPs are required to satisfy the following:
- eduroam
AU National Policy compliance
- the eCS states NROs are responsible for its institutions, and IdPs for their end-users
- AARNet meets its responsibility by requiring National eduroam AU Policy compliance by institutions
- Provide
institutional contacts
- technical contact (2 are recommended, at least one personal), kept current and up-to-date via the eduroam AU AdminTool
- automatic subscription to mail-lists (e.g. technical contact will join the eduroam AU Administrator mail-list for bulk notifications to eduroam AU institutional participants)
- Publication
of Institutional network Acceptable Use Policy (AUP)
- Institutions are required to maintain and make publicly available the institutional network AUP
- requirements for users accessing a visited SP network via eduroam are regarded by the IdP as the same as required on the home institution network, and same consequences for non-compliance apply
- IdP and SP network AUP’s are assumed to be reasonably equivalent
- RADIUS
server deployment supporting end-user traceability
- IdP’s recognise the need and provide the means for associating an access event at SP with an authentication event at an IdP based on RADIUS and network logs provided by the SP
- Time synchronisation of servers, and recording of log timestamps in UTC, the eduroam username, and end-user device MAC (Calling-Station-Id attribute)
- RADIUS server log retention for the time required by the eduroam AU National Policy
- Maintain
accuracy of the institution’s eduroam AU deployment information via the eduroam
AU AdminTool
- Implicit consent to deliver basic data (institution, realm, contact, hotspot locations) to the Global eduroam database
- Publication
of an institutional eduroam participation webpage
- Enable visitors and local users to use eduroam and understand network capabilities without seeking local support
- Provide
local support & training of support staff
- for both visitors and local users
RADIUS Server Implementation
Institutions joining eduroam will often already be using IEEE 802.1x internally, and will have a RADIUS Server deployed already for other purposes.
Configuration of the RADIUS Server for both IdP and SP operability is described in the eduroam AU Technical Specification.
For institutions requiring deployment of a RADIUS server, factors in choosing a RADIUS Server implementation are documented in JISC’s “RADIUS Server Choice Guide for eduroam”.
Identity Provider
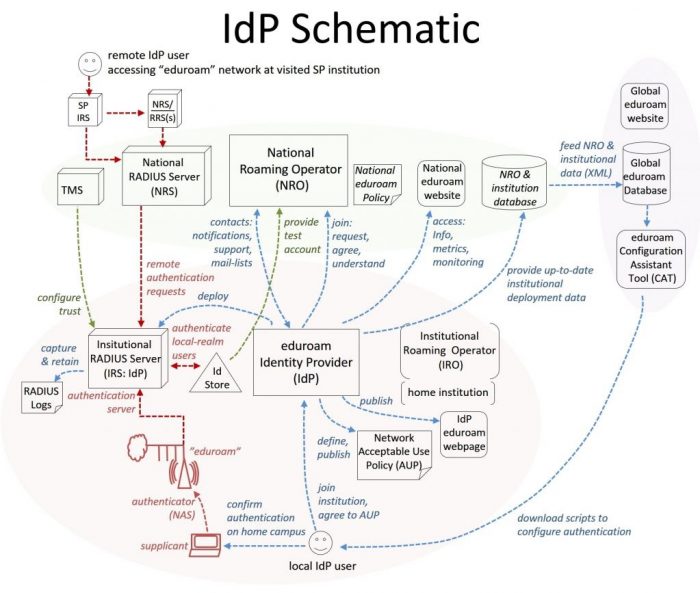
IdPs authenticate users based on access requests for their designated ‘realms’. eduroam end-users have credentials managed by their ‘home institution’ operating as an eduroam IdP. The home institution’s RADIUS servers perform authentication for their own end-user’s authentication requests via its institutional authentication service. Home institution’s end-user authentication requests arrive either from local wireless infrastructure (their users accessing their home institution “eduroam” network on their home campus), or remotely via national RADIUS infrastructure (their users accessing the “eduroam” network of a visited institution).
The following schematic illustrates the IdP participant role:
Pre-requisites
The following are pre-requisites for IdP participation:
- Effective, secure and tightly administered identity management and authentication system, with end-users educated in basic cyber-security
- IT infrastructure & skills capability required to deploy an IEEE 802.1x “eduroam” network host and deploy & maintain the RADIUS server providing IdP operability
- IT support capability (staffing, support request handling mechanism) required to provide support for the institution’s eduroam users as they travel and connect to SP institution eduroam networks
- A published network “Acceptable Use Policy” with the institution’s end-users being ‘contractually required’ to conform to the AUP.
- A website capable of hosting a webpage describing the institution’s IdP participation in eduroam AU.
It is also highly recommended that IdPs operate an “eduroam” network at least for local users, enabling local users to undertake and confirm their eduroam authentication configuration while on their home campus.
Operational Requirements
In addition to the general requirements above, an eduroam AU IdP is required to:
- Determine
local realms for which local RADIUS servers will be configured to authenticate
- multiple local realms may be handled
- realms should be institutional domain names with country-coded top-level DN part (e.g. “student.myuni.edu.au”)
- Determines
EAP methods supported (based primarily on Identity Store characteristics)
- Select MSCHAPV2 inner-authentication if capable, otherwise PAP
- Populate Chargeable-User-Identity (CUI) attribute
- RADIUS
server configured for eduroam authentication
- Receive authentication requests from the National RADIUS Servers (institutional end-users travelling to SPs and connecting to the visited institution eduroam network) and perform remote authentication
- Authenticate institutional end-users connecting to eduroam locally (authentication requests from local wireless infrastructure) to enable local eduroam network access, or at least confirmation of end-user device eduroam configuration
- educate
local users in configuration of eduroam on their devices
- configure on the institution’s home campus
- use scripts available from an automated system performing secure configuration (e.g. eduroam CAT)
- If CUI is not provided, recommend against configuring an anonymous outer-identifier
- ensure users are educated regarding the requirement for mutual authentication (i.e. their device authenticating the home IdP)
- Logging
end-user authentication data
- RADIUS logs, capturing and retaining:
Timestamp (UTC), (outer and inner) User-Name, Chargeable-User-Identifier,
Calling-Station-Id, Reply-Message, Operator-Name, NAS-IP-Address
- Identity Store logs as required to facilitate end-user association with the RADIUS logs
- RADIUS logs, capturing and retaining:
- Enable
troubleshooting by NRO
- Provide institutional test account for each realm
- Account for each supported realm
Operational Decisions
Institutional Realm(s)
Realms should have a country coded top level domain name part in order to avoid need for exception configuration in regional RADIUS servers.
Authentication Protocols
The two pairs of authentication protocols used most commonly are
- PEAP/MSCHAPV2
- TTLS/PAP
It is preferable to user PEAP/MSCHAPV2 if possible, as a challenge-response protocol will remove the possibility of leakage of credentials.
Factors in deciding which authentication protocol to implement are described in GEANT’s How to deploy eduroam on-site or on campus (ADVANCED).
RADIUS Server Certificate
The IdP RADIUS server certificate is the basis for mutual authentication. The factors in the choice of RADIUS Server Certificate is documented in Server Certificate Practices in eduroam.
Service Provider
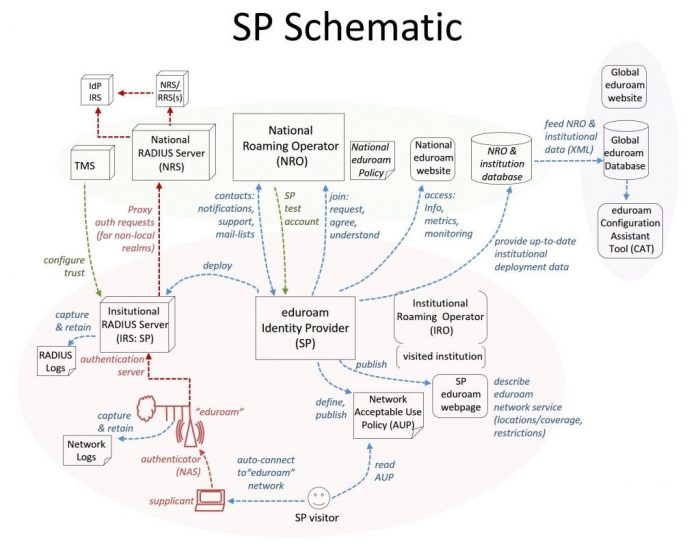
SPs provide the “eduroam” network which eduroam end-users can access as they travel. That is, they provide the network infrastructure and internet connectivity for an “eduroam” network, configured to use IEEE 802.1x authentication, and provide a local “authentication server” (RADIUS server) which proxies requests for visitors (authentication requests with non-local realms) to the national RADIUS server.
The following schematic illustrates the SP participant role:
Pre-requisites
The following are pre-requisites for SP participation:
- The institution must be able to describe the ‘business case’ that will motivate the institution contributing the effort required to comply with policy requirements, including bearing the cost of eduroam network traffic.
- Well-functioning and performing wireless infrastructure
- A published network “Acceptable Use Policy”
- IT infrastructure & skills capability required to deploy an IEEE 802.1x “eduroam” network host and deploy & maintain the RADIUS server providing SP operability
- IT support capability (staffing, support request mechanism) required to provide support for eduroam users
- A website capable of hosting a webpage describing the institution’s participation in eduroam AU as an SP.
Requirements
In addition to the general institutional requirements, an eduroam AU SP is required to:
- Reliable
and high quality wireless service configured for IEEE 802.1x and broadcast
“eduroam”
- Institutions should be aware of overlapping “eduroam” hotspots of other institutions, and determine how to avoid any associated issues
- Deliver
a reasonably unconstrained network service for “eduroam” visitors
- Deliver
recommended ports opened & services available
- Provide as open network access, and as much bandwidth, as permitted by local policy
- Refer to the recommended ports list in the eduroam AU Technical Specification
- Utilise VPNs for segregation of visitor eduroam from local eduroam users
- Deliver
recommended ports opened & services available
- Configure
proxying of visitor authentication requests in the institutional RADIUS Server
- Proxy to NRS servers (with fail-over)
- Support
required RADIUS attributes
- Proxy only the minimum set of attributes required by eduroam (see list of attributes described in the Technical Specification)
- Populate the “Operator-Name” attribute
- Populate the “eduroam-SP-Country” attribute
- Request the “Chargeable-User-Identity” attribute from IdPs
- Do not proxy VPN specific attributes
- Accounting
- Do not proxy accounting requests
- Logging
data
- RADIUS logs
- Timestamp (UTC), (outer) User-Name, Chargeable-User-Identifier, Calling-Station-Id, Reply-Message, Operator-Name, eduroam-SP-Country, NAS-IP-Address
- Network
logs
- NAT, DHCP logs as required to associate the an allocated IP address to the user-device MAC address
- RADIUS logs
- Enable
troubleshooting by NRO
- Configure trust for NRO Test&Monitoring Client in each RADIUS server
Operational Decisions
Wireless Infrastructure
Wireless infrastructure must be configured to broadcast the “eduroam” SSID. If there is an eduroam hotspot area of substantial overlap with another institution’s eduroam network, the institution must decide whether or not to broadcast eduroam in that zone. Any risk of degraded eduroam performance should be avoided, or at least described on the institution’s eduroam AU participation webpage.
Network Service
The eduroam network service recommended to provide a consistent quality of service is described in the Technical Specification.
SP institutions may have local policies or infrastructure requirements that result in network access restrictions. Any differences to the recommended service or restrictions must be described on the institution’s eduroam AU participation webpage.
Wired Network use of eduroam
eduroam is primarily used for Wi-Fi access at institutions, however it is readily available for wired connections too. (In fact the RADIUS protocol was originally devised prior to prolific wireless availability, and is referred to as “port based” authenticated access via switches with RADIUS capability. The institution should describe any availability of wired eduroam network access on its eduroam AU participation webpage.
Deciding to Join eduroam AU
In presenting a case for joining eduroam AU to institutional management, beside the work required to satisfy the role requirements described above, the following are proposed as useful considerations.
Benefit to Institutions of Participation in eduroam
The benefits to an institution in participation in eduroam include:
For an IdP:
- Users being able to easily access the network of global eduroam SPs and achieve secure, performant network access (compared to any public Wi-Fi that may be available)
- Ability to be able to provide support, collaborating with the visited site and eduroam operators, to users when they visit another institution.
For an SP:
- No requirement to provide administrative effort to providing network access for visitors (e.g. creating account, hosting an access administration website)
- Provision of a good network access experience to visiting research and/or education users, enhancing the value of visiting to the users.
Cost of Participation
Cost of access to the eduroam network at a visited institution is borne by the visited institution, the user community being the closed but very large global community of research and education users.
Risks of Participation in eduroam
For an IdP, the risks of participation in eduroam include:
- Leakage of user credentials (if users are not diligent in configuring their devices, or trust a rogue ‘home’ RADIUS server)
- Requirement to take action against a user who does not comply with the home institution AUP, reported by a visited institution, applying the same consequences that would be applied if the user performed the actions on the home institution network.
For an SP, the risks of participation in eduroam include:
- Visitor not complying with the visited institution network AUP
- Reliance on a separate institution (IdP) to hold the end-user to account for any abuse of the network
- Costs associated with end-user network traffic

