Purpose
eduroam AU institutions participating as an eduroam identity provider (IdP) are responsible for their users in their use of eduroam. An important aspect of this use is secure and consistent configuration of end-user devices for eduroam access and authentication.
In order to ensure users globally configure their devices using recommended security best practices and in a consistent way to assist troubleshooting, the European eduroam Operations Team has developed and hosts an eduroam Configuration Assistant Tool (CAT). This tool generates scripts for all major end-user device platforms, with institutional configuration data obtained primarily via the Global Database.
The CAT is recommended to be used by eduroam AU institutions participating as an eduroam Identity Provider (IdP). The only exception should be those institutions that provide another automated means of device configuration for eduroam access/authentication.
The CAT also provides institutional administrators with the ability to trigger test authentication events to the institution’s configured realm(s) from European eduroam infrastructure. This is one of the tools available to test eduroam AU IdP operability.
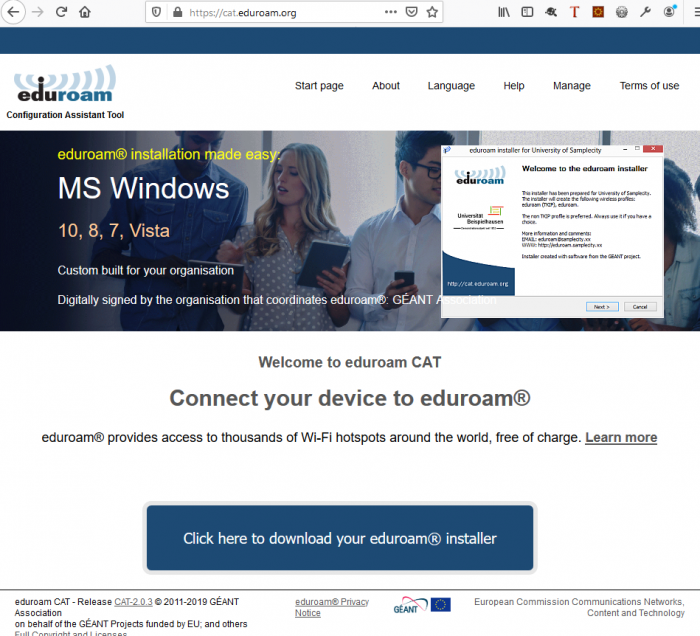
Functionality Overview
There are 3 interfaces available in eduroam CAT. User guides (PDFs) for end-users and institutional administrators for CAT v1.x linked below. The information in those guides is provided for CAT v2.x on this webpage.
- eduroam AU national roaming operator (NRO) (AARNet)
- eduroam AU institutional administrator
- eduroam end-user
Following the IdP institution’s eduroam RADIUS server deployment, the eduroam AU institutional on-boarding process includes a step for institutional administrators to access and configure CAT. This follows AARNet confirming completeness of institutional data in the eduroam AU AdminTool, and enabling institutional data to be sent to the Global Database, which then propagates to the CAT tool. Institutional data entry must have been performed earlier during institutional on-boarding via the eduroam AU AdminTool.
During on-boarding, institutional administration of CAT involves:
- Completion of configuring CAT ‘profiles’ for each of the institution’s realms (utilising institutional RADIUS server related data which may be different for different configured realms), specifically the addition of RADIUS server certificate information.
- downloading and testing generated device configuration scripts
- using CAT test facilities to confirm reachability of the institutional realm
The final stages of IdP institutional on-boarding includes a user education which informs institutional users of the institution’s participation in eduroam AU and user benefits of eduroam, and the recommendation and rationale for use of CAT scripts to configure end-user devices.
Configuration Script Security Practices
The CAT generated device configuration scripts employ two important security practices:
- Ensure home-institution RADIUS server authentication – this is critical to avoid susceptibility to a man-in-the-middle attack (eduroam entails automatic connection to infrastructure), which would potentially result in stolen credentials and/or session hijacking.
- No-prompt for trust of a newly encountered certificate – this is important to prevent human error in wrongly accepting to trust a connection with a RADIUS server which enables a man-in-the-middle attack.
Use of Alternate Device Configuration Automation
Some institutions may have their own local device
configuration automation system. This system should be configured to configure
user-devices in an equivalent way, to ensure consistent configuration of
eduroam connected devices, thereby facilitating efficient end-user support.
Institutional Administrator Use of CAT
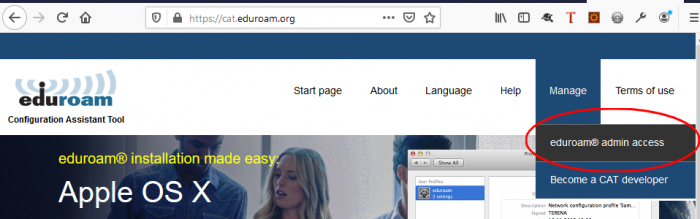
Access to CAT
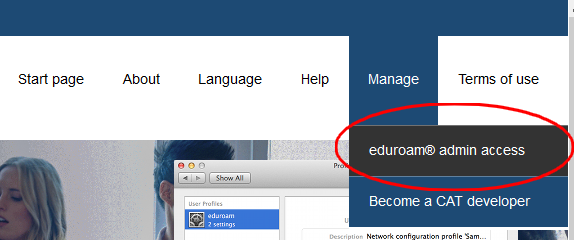
Both NRO and Institutional Administrators access CAT’s administration interface via the “eduroam admin access” menu item.
Institutional Registration
In order for an institutional administrator to be able to use the eduroam Configuration Assistant Tool, AARNet as eduroam AU NRO needs to register the institution with the CAT service, and invite the individual administrators for the institution who will be authorised to access and modify their institutional configuration data.
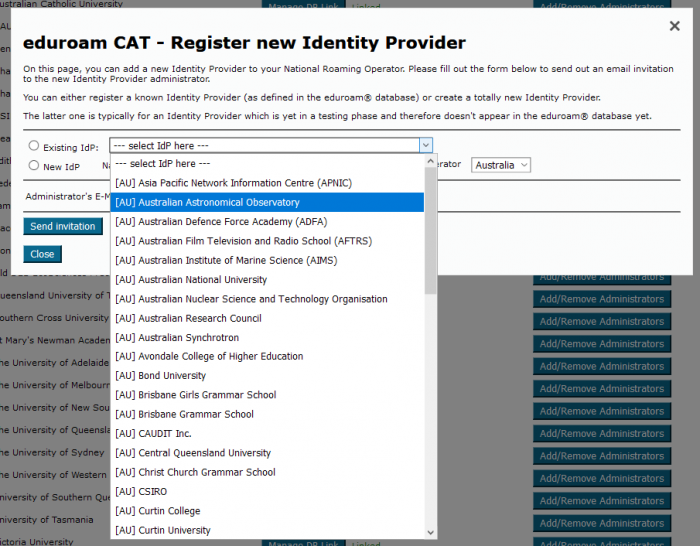
The administrator account email address will be added by AARNet, resulting in an email invitation for institutional administrator access CAT to be sent.
CAT Administrator Invitation
Following institutional information being added to the eduroam AU AdminTool, the institutional data being sent to the Global Database, and data ingest by CAT from the Global Database, AARNet will advise the designated institutional administrators of readiness to configure CAT.
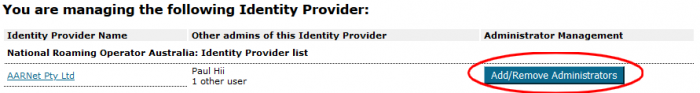
Inviting Additional Administrators in CAT
Registered institutional administrators can invite other users from their institution to access CAT as an administrator.
For existing institutional participants not having access to CAT configured, an institutional eduroam administrator wishing to make use of CAT should request access via support@eduroam.edu.au, including the list of administrators that are authorised to access the institution’s CAT configuration pages.
An email is sent to the administrator with a link to activate their access, with content similar to below.
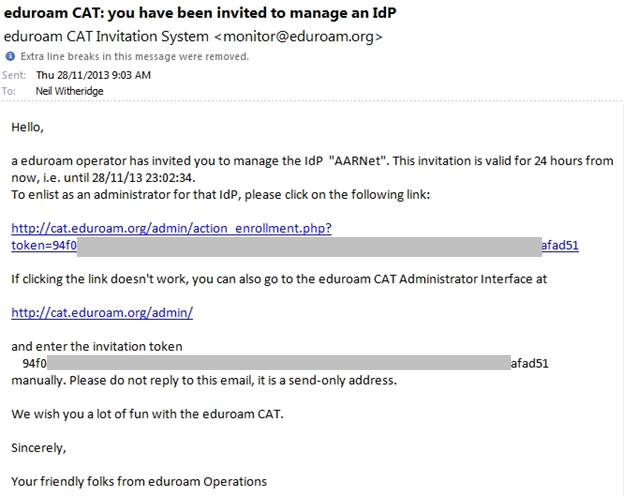
Once this invitation is acted upon, the invited institutional administrator can use CAT to administer their institution’s configuration in CAT.
Accessing CAT as an Administrator
The CAT hompage is https://cat.eduroam.org. Administrators click on the “Login as Administrator” menu item.
Logging in via SAML Authentication
An initial page advising that you need to receive an invitation in order to access the CAT.
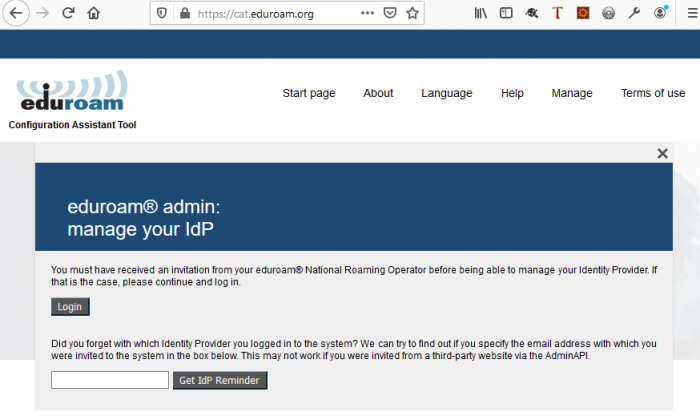
Click on Login to continue to login via SAML.
AARNet operates a SAML proxy in order to provide access to eduroam related services. Currently the proxy is accessible under the “Experimental” tab of the global eduroam SAML discovery service which provides for selection of the SAML identity provider.
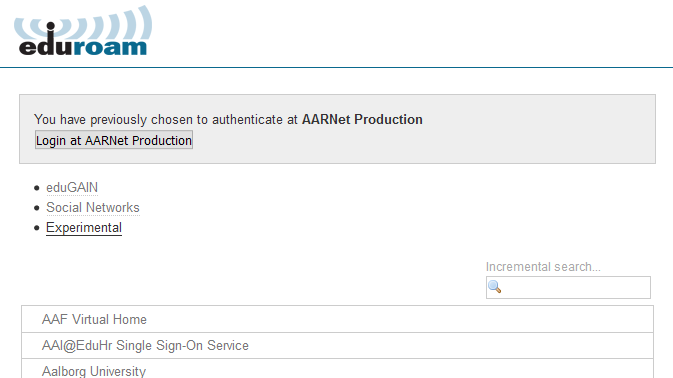
Following clicking on Experimental, select “AARNet Production” as the identity provider.
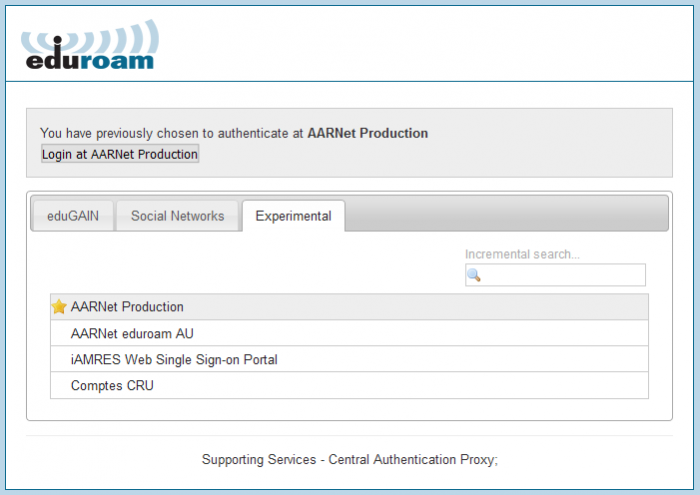
Select your institution from the list of available institutions in the AARNet SAML IdP list

Use of the AAF Virtual Home Organisation
If your institution is not a member of the AAF, or does not operate a SAML IdP with trust configured in the AARNet SAML Proxy service, you will need to have accounts created under the AARNet group in the AAF Virtual Home Organisation.
Setting up a VHO account is described in a separate document.
Once the AAF VHO account has been created, the AAF VHO icon needs to be selected in the AARNet SAML Proxy discovery service.

CAT Administrator Home Screen
Once logged in, an Administrator is presented with the CAT home page which provides a link to their institutional administration page.
Initial Administrator Actions
Institutional Data Confirmation
Institutional administrators should first confirm the data stored in CAT which has been ingested from the Global eduroam Database.
The basic information needed to configure your device ‘supplicant’ for IEEE 802.1x authentication to the eduroam network is:
- SSID (should be “eduroam”)
- Outer authentication method (PEAP recommended)
- Inner authentication method (MSCHAPV2 recommended)
- Home RADIUS Server certificate information (for authenticating your home RADIUS server)
This information will be read from the global database, however the
administrator should confirm this information via the CAT GUI.
Identity Provider Configuration Overview
Below is the Identity Provider Overview for AARNet.
The top section of the page displays Identity Provider general settings, followed beneath firstly by Avaliable Support Actions.
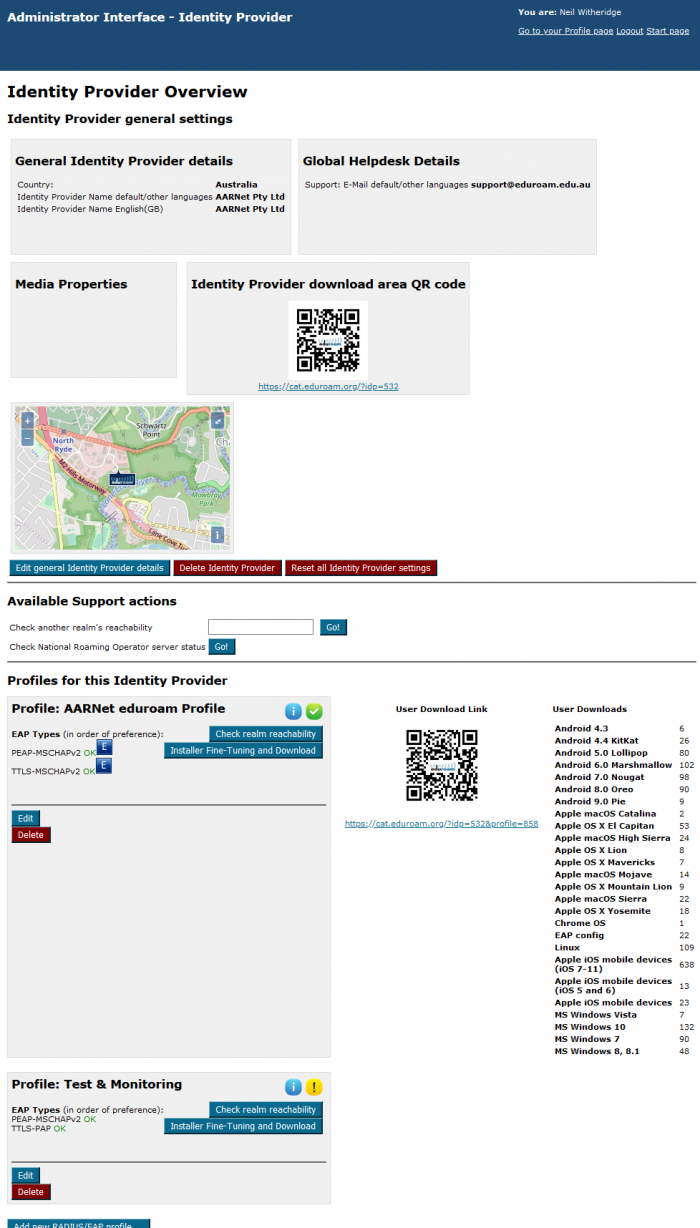
Beneath “Available Support Actions” are the profiles configured for this IdP. A profile corresponds to a supported realm, each identifying which EAP types are supported. Global EAP Options show AARNet’s home IdP RADIUS Server certificate information.
Notice that AARNet has two profiles/realms listed. One the main institutional realm, “aarnet.edu.au”, and the other the eduroam AU Test&Monitoring realm “test.eduroam.edu.au”.
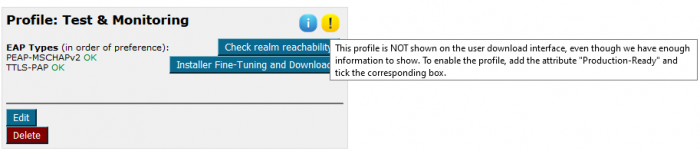
Notice also that the Test & Monitoring realm is not a production realm for AARNet, and does not appear on the AARNet institutional download interface where AARNet users get their scripts from.
Edit General Identity Provide Details
The information in the general IdP details section should be entered automatically based on information available from the Global Database, data ingested from the eduroam AU AdminTool.
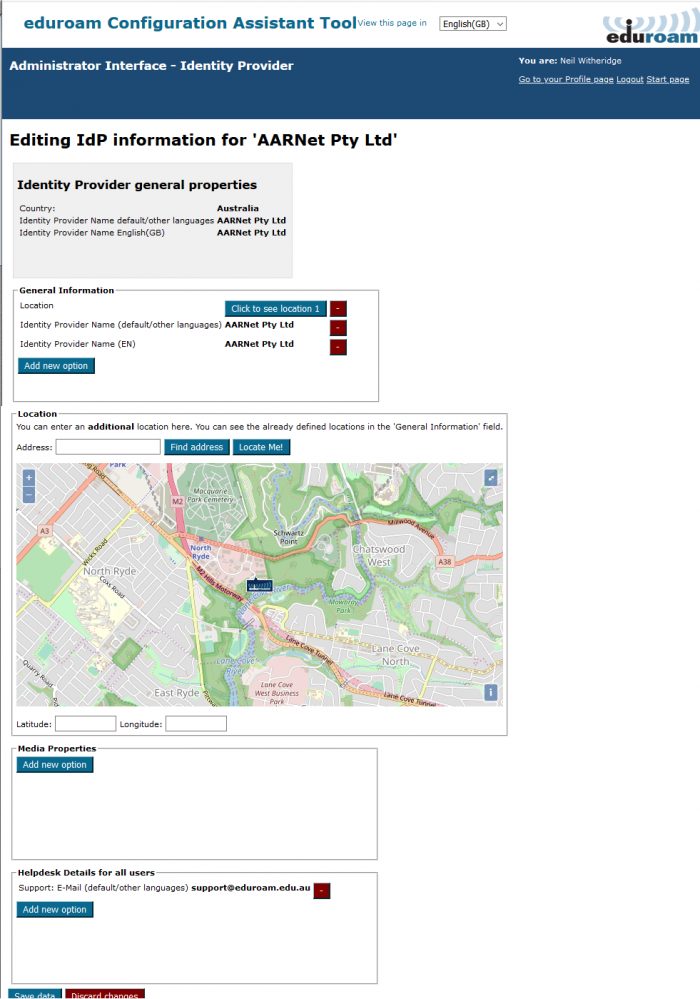
Edit Profile
Within each profile there is an “Edit” button that enables the Profile to be edited. Institutional administrators need to add home institution RADIUS server certificate information via this interface in order for scripts to be generated.
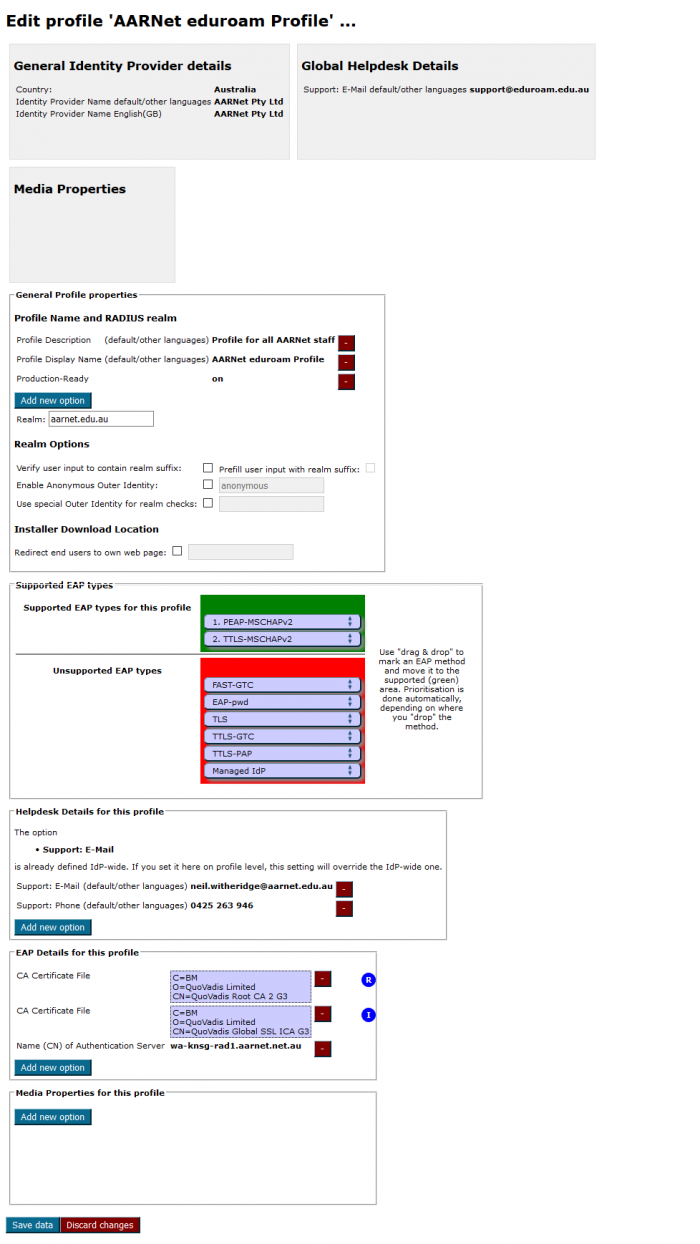
CAT ‘Profiles’ are prepopulated for each realm included in information ingested from global database. In the AARNet case, the “Test & Monitoring realm profile was added separately, the Test&Monitoring realm not populated via eduroam AU AdminTool hence not in the eduroam Global Database.
Scripts are generated for each fully configured realm, the realm profile determining the configuration information in the configuration scripts (e.g. EAP type).
Adding Institutional RADIUS Server Certificate Information
The information that needs to be added by institutional administrators is the institution’s RADIUS server certificate subject name and the signing CA certificate(s).
Enter certificate data under:
Edit Profile
-> “EAP details for this profile”
–>Add new option
First select “CA Certificate File” and then “Browse” to browse to the CA Public Certificate file, then select “Name (CN) of Authentication Server” and add the CN part of the “Subject” field of your home institution RADIUS server certificate.
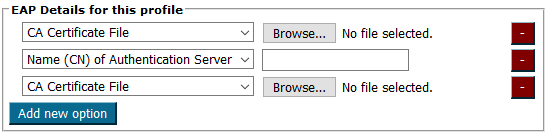
As an intermediate certificate is also required, this must be added as another “CA Certificate File”.
Click “Save data” once updates are made, the resulting “EAP Details for this profile” being:
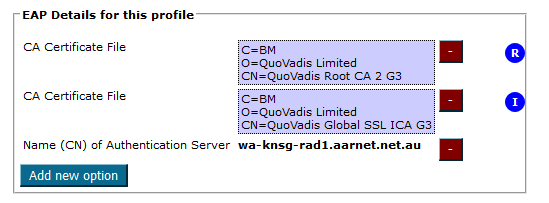
Accessing and Testing Generated Scripts
Confirming Script Correctness
It is recommended that institutional administrators download the Linux version of the authentication configuration script and read the shell script and gain an understanding of the configuration.
It is recommended that institutional IT staff test a subset of available scripts (at least those for platforms with majority use in the institution) to ensure that the configuration data is correct and to ensure that configuration on the home-campus works properly.
User Education
Following confirmation of the CAT scripts’ correctness, institutional administrators should undertake an education campaign which advises institutional users about CAT and the importance of downloading and using the CAT scripts for their device configuration.
Information on using CAT should be provided on the institutional eduroam webpage.
In particular, the importance of end-user devices being configured to authenticate their home institution RADIUS server should be emphasized. Users need to be aware that if they choose some other method of configuration (e.g. the default operating system connection to 802.1x networks), or if authentication is manually turned off in the end-user device configuration, or a user doesn’t check certificate details when asked to validate a newly seen certificate, then the user is at risk of having their eduroam session hijacked or credentials (specifically if using PAP authentication) compromised by a ‘rogue’ access point/RADIUS server.
User Configuration on the Home Campus
It is important that users understand the importance of configuring their device while on their home network, in order to ensure as smooth a possible configuration experience. Note that IdP institutions should enable users to configure / confirm their authentication on their home campus.
Providing Configuration Scripts to End Users
Advising End-Users of Configuration Scripts
Once all information is provided to CAT, administrators must advise institutional end-users regarding the use of the scripts. As a minimum, this should include a brief description of the CAT service and a link to the CAT homepage.
Either a CAT link & simple instruction can be provided to users from the institutional eduroam webpage. It may also be deemed appropriate or convenient for institutions to download CAT scripts and make them available locally.
End-users need to be aware of is the need to correctly identify their Home Institution when they access the CAT download page. There is scope for confusion whereby users may think they need to download scripts for the visited institution, so emphasis should be given that the Home institution is the correct script to install for all eduroam use.
User Devices without CAT Scripts
The CAT generates scripts for the vast majority of end-user device platforms. In the event of a user using a device for which there is no CAT script, the basic information to configure and guidelines for and warnings related to security best practices should be available via the institutional eduroam webpage.
End-User Access to the CAT Service
Users access the eduroam CAT service at https://cat.eduroam.org/ and click on the “Click here to download your eduroam installer” link.
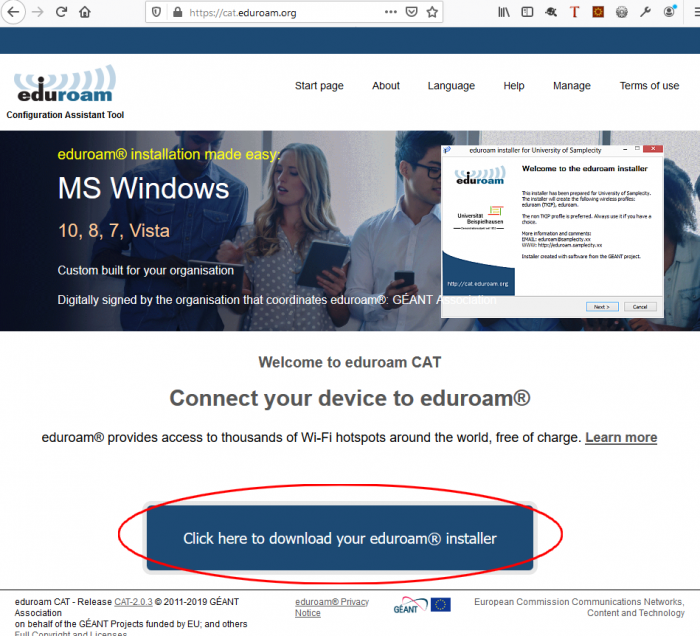
Selecting Your Institution
Selection of the home institution is required, and this is assisted by the location awareness of eduroam CAT.
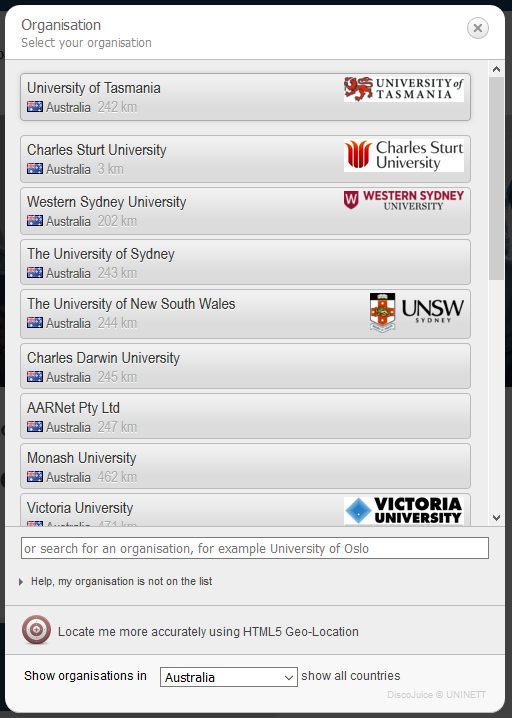
With location awareness enabled, eduroam AU users should be presented with a display of AU institutions.
Alternatively, users can enter their institution name in the search field
Note that a user’s institution must have registered to use CAT to be displayed and be selectable, and have scripts available for download
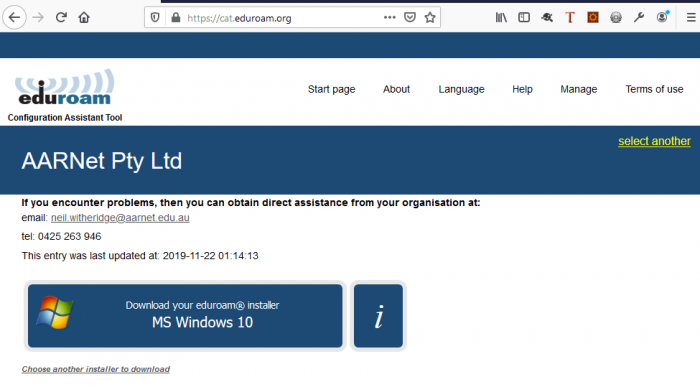
Upon selection of the institution, the download corresponding to the OS being used to access CAT is displayed.
The device will be detected from the http transaction, and the appropriate download link displayed.
The full list of scripts can be displayed also, and any one of them downloaded.
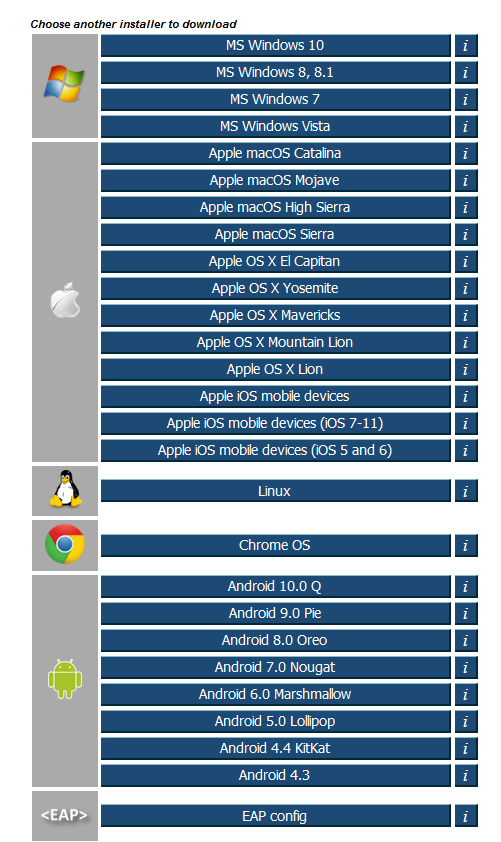
Downloading a Configuration Script
When a link e.g. Apple OS X Lion is clicked, the recommended authentication method is displayed
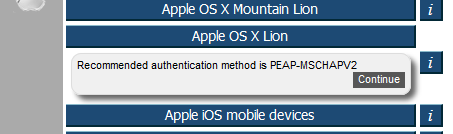
When the [Continue] button is pressed, a welcome message is displayed and a download prompt is provided (exact appearance dependent on your browser, below is prompt from Firefox on Windows 10)
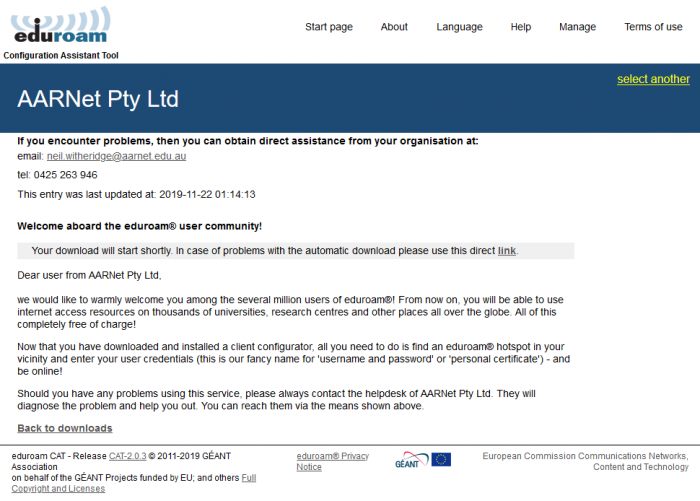
Click on resulting Save File prompt (unless advised to do otherwise in the instructions provided – see the next section).
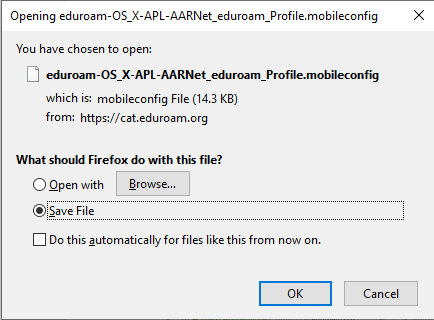
Using Configuration Scripts
The way in which scripts are applied is dependent on the end-user device type,
The information button on the installer download page describes how to execute the configuration script on each platform covered.
For example, if the information button to the right of the link to the Apple OS X Lion script is pressed, the instructions displayed are
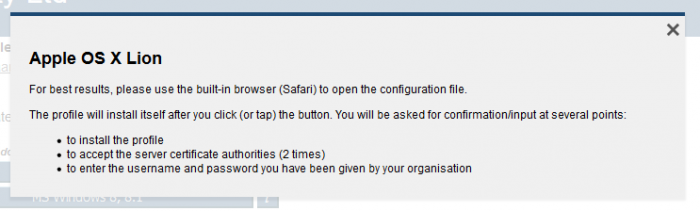
CAT Identity Provider Test Facilities
There are several IdP test facilities available from the CAT, which involve triggering test authentication events to the institution.
The Profile page has a button which is used to check for reachability of the institutional realm associated with the profile.
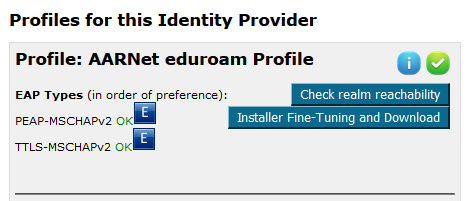
Click on “Check realm reachability” to commence the static connectivity test.
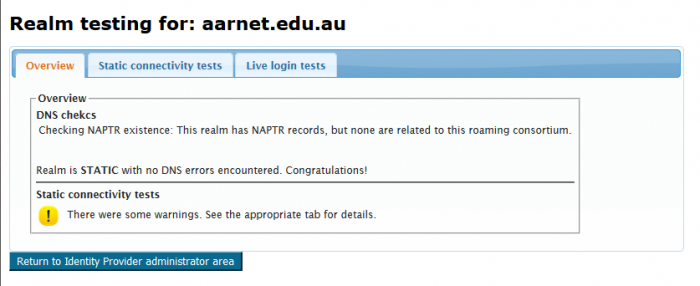
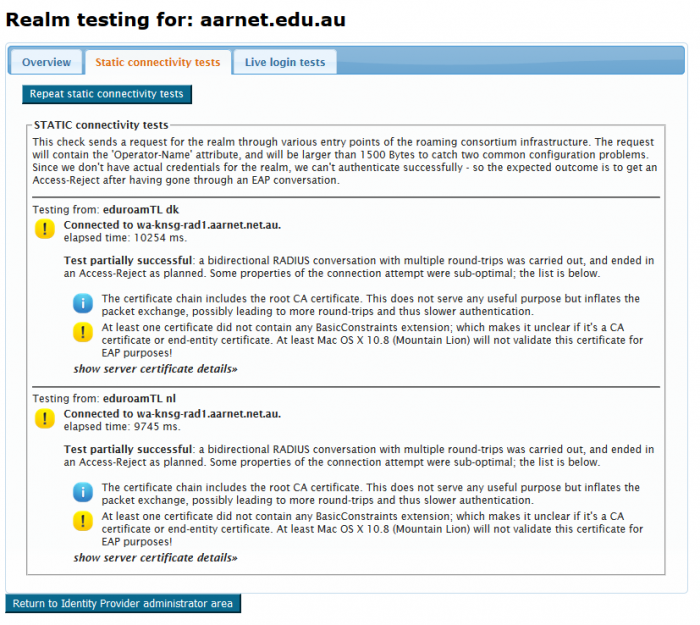
Logs provided under “Static connectivity tests” provides helpful information regarding the IdP configuration.
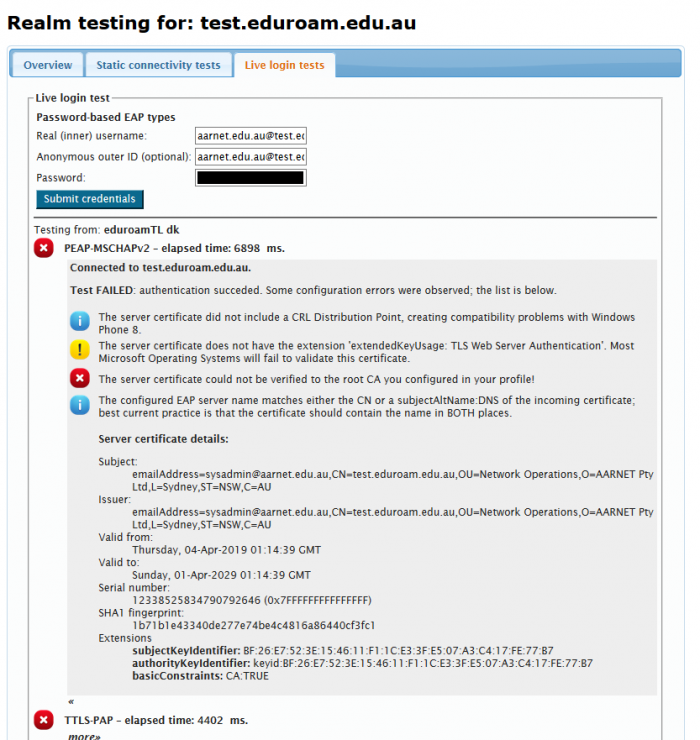
Tests using institutional accounts can also be conducted using the Live login tests tab.
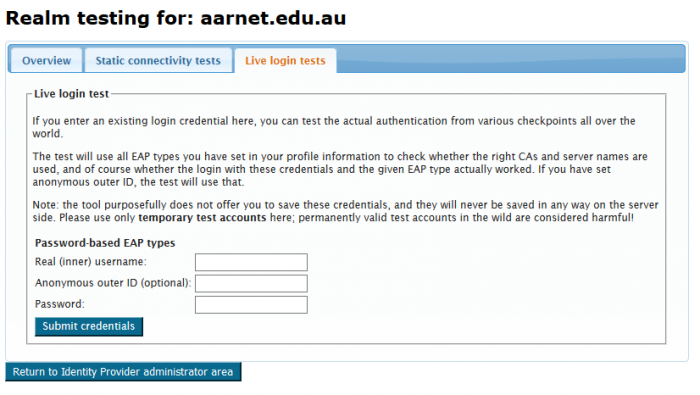
Testing a user provisioned on the eduroam AU Test and Monitoring Server provides the following output (truncated, password removed):
SP Institutional Use of CAT
The CAT tool provides end-user configuration scripts, and test facilities for IdP institutional administrators to test reachability of their realms. It is not used to test SP functionality, hence has no part in SP-only participants on-boarding or operation.

